The problem of data recovery after ransomware that encrypts files has increased, with more and more cases recently. Help in these cases is not a trivial task.
Challenges in Data Recovery for Ransomware Encrypted Files
Let’s consider some sides of this problem. Ransomware usually encrypts the most-used data such as photos, videos, office files, databases, etс. Ransomwares can give different extensions to encrypted data; they are considered as a same mechanism that uses similar algorithms.
Files are encrypted with cryptographic algorithms. Keys consists of a public key and a private key. The public key is generated on the victim’s PC, while the private key is kept in secret and only the fraud perpetrator knows it. The combination of public key with private key is special for each case. It’s impossible to decrypt data without a private key. Solutions offered by well-known anti-virus developers are likely to focus on selection of the private part of the key, by brute force or special heuristic analysis.
We haven’t faced a practical experience of payment to obtain decoder software, but our customers state they had such experiences. Let’s drop the moral side of this problem, such as whether to pay or not to pay. It’s obvious there’s no need to encourage malicious users, but everyone has their own view as to the importance of data.
However, there have been cases of partial decryption of files. Each case was special. Success is possible only if ransomware encrypts not a whole file, but only part. Such an attitude from the hacker has a logical explanation. As data volume increases, time to encrypt files increases, so the risk to be discovered increases as well. That’s why we think only an important part of the data is encrypted, rather than all of it.
Practical Case: Recovering Data from Ransomware Encrypted Files
Here’s a practical case. A ransomware encrypted the beginning of the file, some fragments in small size in the body of the file and added its technical information at the end of the file. We faced some tasks on this step:
- to determine a correct end of the file, carve ransomware’s addition;
- to determine the size of damaged header;
- to determine the location and size of encrypted fragments in the body of the file.
The solution with end of the file was simple.

It was more complicated with the header because it’s often special. It’s possible to replace it with another one with little change from a similar correct file. In our case, the file headers were changed using XOR and modifying some bytes.
We couldn’t find the solution with encrypted areas in the file. The private part of the key is unknown, data is unique so it’s impossible to match it. We made the software that automates the process of correcting the beginning of the file and end of the file.
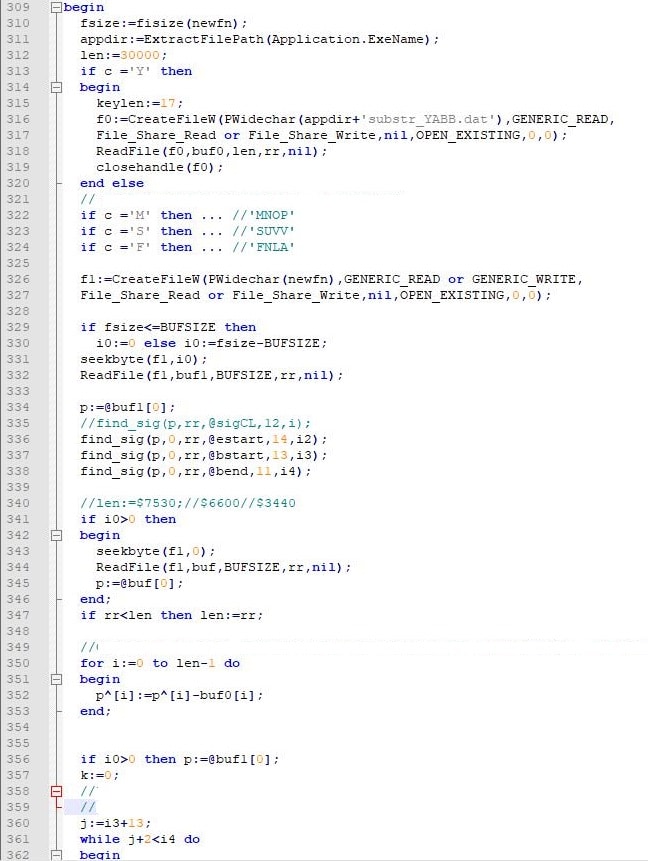
We got correct video with some artifacts and correct or partly correct office files. The main fail was with JPEG files. Information was compressed so even little damage leads to the damage of the whole file.
We made the next algorithm. Considering the location of encrypted data is known, we can define the line in the photo where there’s a damaged fragment and replace it with the previous line or the next one.
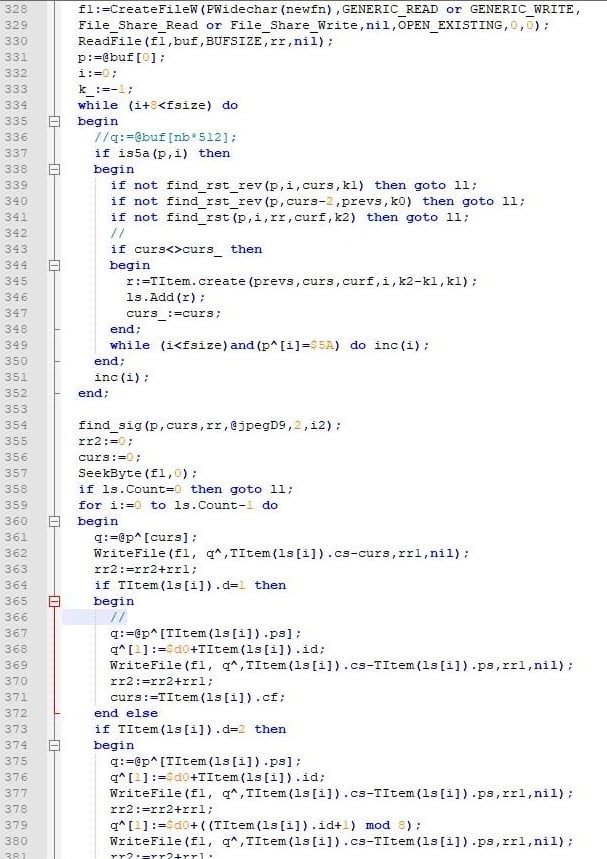
The substitution usually was invisible, but sometimes we got curious photos. Such approach let us recover some photos to an acceptable level.


Need to admit there’s one more approach of data recovery. It’s a search among the deleted files and analysis of free space.
Let’s draw the conclusion. If a ransomware encrypted your files, it’s not always a “sentence.”
Just don’t give up!
FAQ
Are the files encrypted or a whole partition?
We have had both cases in our experience.
If files are encrypted, we recommend you recover data from FreeSpace partition (ransomware usually misses this area).
Why will it succeed?
Data copies could be deleted, moved or create temporary files. So it’s necessary to make analysis.
It’s a difficult case when a partition is entirely encrypted. In the future it will occur rarely.
Why do we think so?
The volume of storage devices increases. As a result, time spent for encryption will increase as well. This will make it more difficult for hackers to achieve their goals.
Is it possible to recover data if a whole partition is encrypted?
If the algorithm of encryption is cryptographic and the key is unknown, we won’t be able to help.
How can you determine whether an algorithm is cryptographical or not?
Usually the algorithm of encryption is unknown. So it’s difficult to give a definitive answer. There’s a choice to search markers.
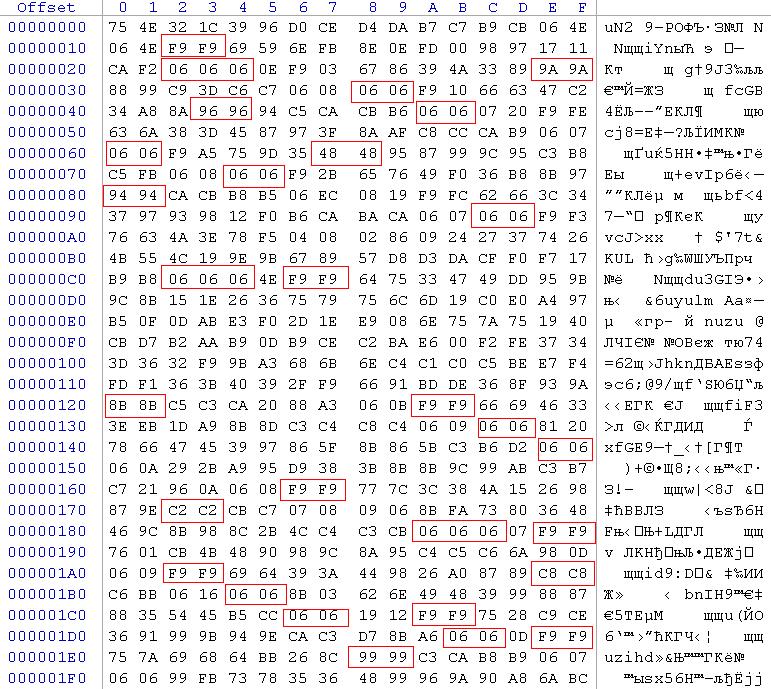
In this case, we define XOR with some additions.
How to determine XOR is used?
It’s necessary to take two or three files of same type and compare them. The presence of coinciding parts and further analysis will let us make a conclusion about the algorithm used.

A frauder sent the name of algorithm of encryption in a text file. Will it help to decrypt?
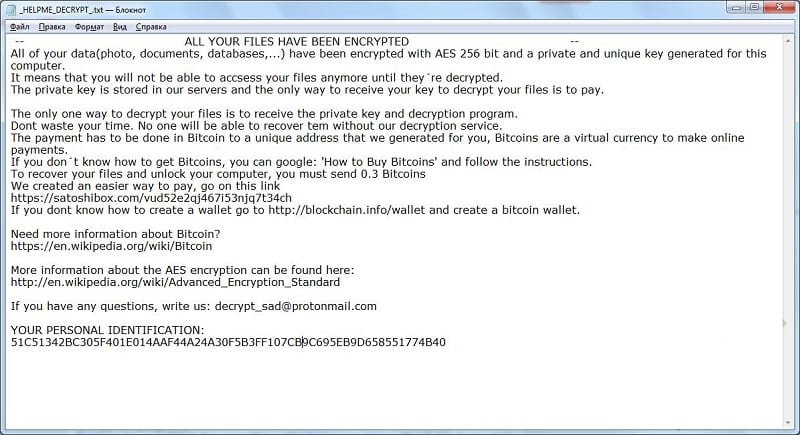
It’s difficult to answer. There are many variations of cryptographic algorithms. The task of key search is the most important.
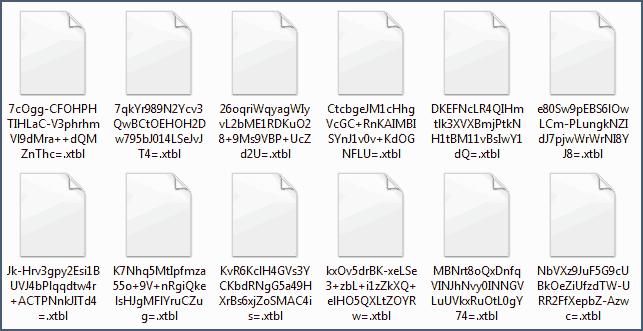
I know a new extension of files that ransomware created. Will it help?
It’s not important what kind of extension it is. There are many options, but they systematize poorly. Most important is what is inside the file.
How can you find the encryption key?
It’s a direct key brute-force or heuristic analysis. But there are few chances.
If there’s ransomware (for example, an email with an infected file), it’s possible to make a test case with prepared PC with a huge volume of data (we need to buy some time). Run a ransomware. While it’s encrypting data, we make some dumps of RAM in short intervals. Compare them and seek patterns.
Have you succeeded in key searching with the help of RAM dumps?
Not yet. It’s just a hypothesis. We can’t check it because users are not ready to pay for such expensive work.
So when is it possible to help if a virus has encrypted data?
It’s possible if files are not entirely encrypted.
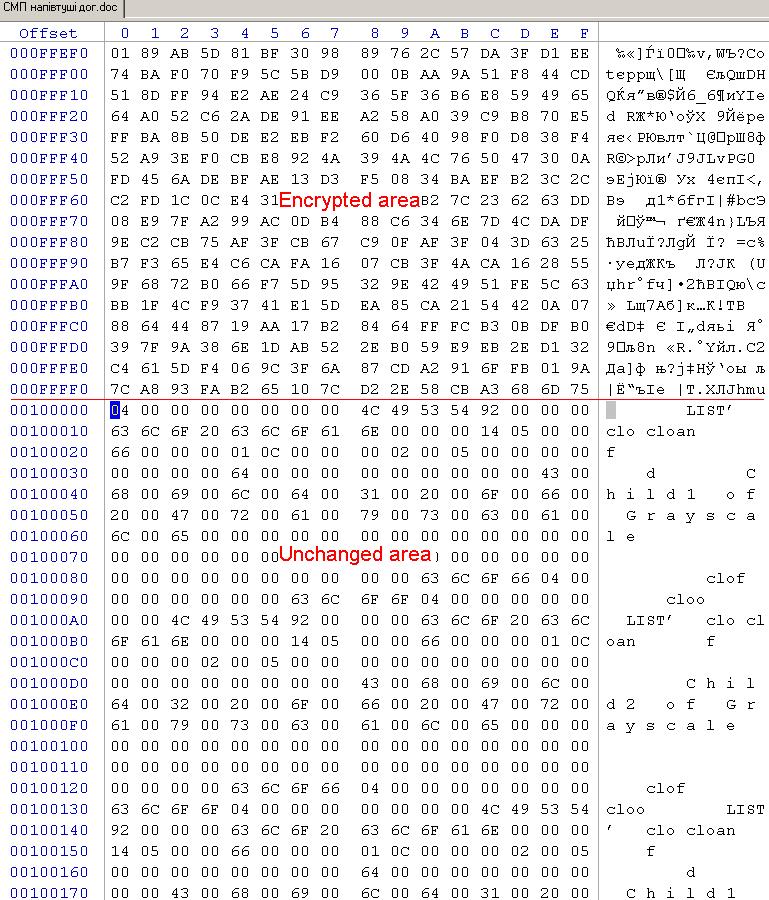
How can you determine that?
You need to find an unencrypted copy of an encrypted file (on another device, for example) and compare them. This procedure should be repeated on some examples. It’s necessary to determine the length and location of encrypted areas better.
If there’s no coincidence, file will be entirely encrypted. The only decision is a key search (vide supra).
If there’s coincidence, part of the user’s data is not encrypted.
What size of file should be taken for comparison?
The more the better. A file’s size has to be more than 10 MB. One of the versions of well-known Petya (NotPetya) encryptor had encrypted only the first MB of data. Files of up to 1 MB were entirely encrypted. Files of more than 1 MB were partly recovered. Look at the fifth figure.
How can you recover data if a file is not entirely encrypted?
There’s no single algorithm for the problem. Everything depends on data file type, length and location of encrypted areas. It’s a creative work for data recovery specialists.
What do you do when you get a case with ransomware?
The algorithm we follow:
to check FreeSpace area
to investigate the ransomware
- we open uncompressed files, for example doc, xls (don’t confuse with docx, xlsx). If you don’t have a correct header of a file, so this file is possibly encrypted
- we search a code 0x00000000 (for example). Such code is often used in uncompressed files and it’s not used in encrypted fragment.
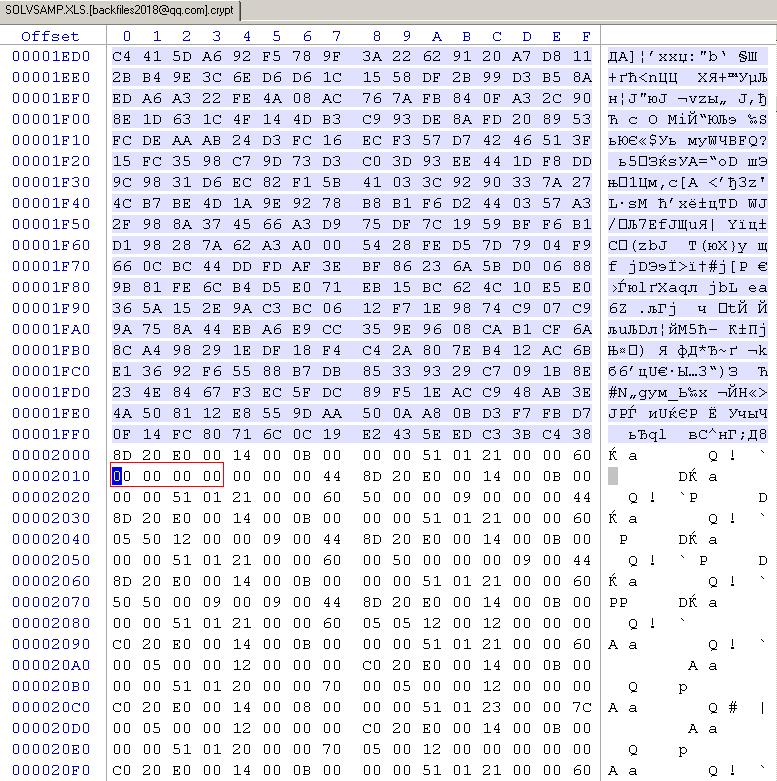
- we ask the customer to provide unencrypted copies of encrypted files from another PC, if possible
- compare them and define the areas of encryption
- in this example at 6th pic ransomware encrypts with blocks 8192 bytes in size.
| Encryptarea | Unchanged area | Encryptarea | Unchanged area | Encryptarea | Unchanged area | … | ID keyransomware |
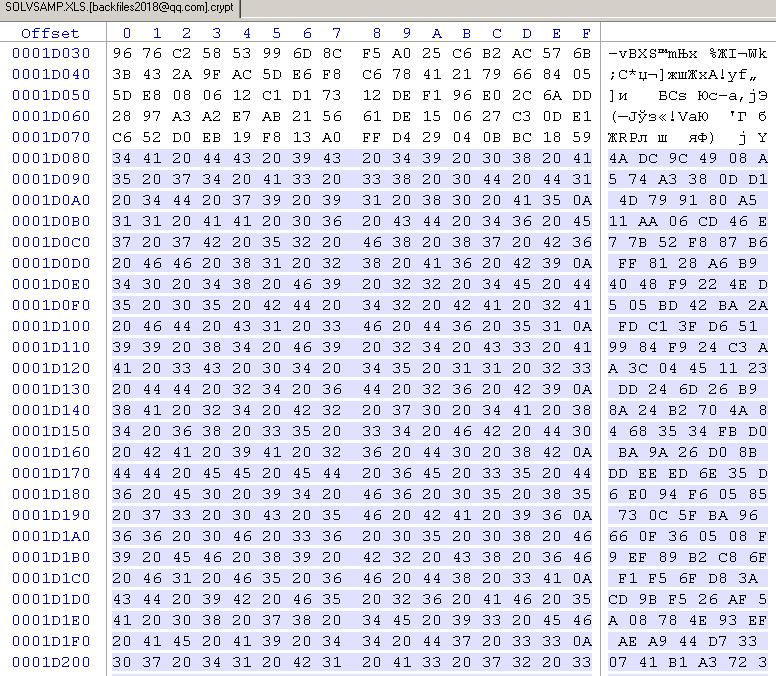
We try to decrypt using various combinations of ID key ransomware and known algorithms of encryption (AES 256, for example). We know that there are a few chances but let’s try.
- we suggest RAM investigation if there’s ransomware;
- we define more exactly what kind of data should be recovered and whether partial data recovery will help the customer;
- we suggest an individual solution depending on a file type.
About the author
Andrey Fedorov is co-owner of 512 BYTE company, the specialist in data recovery, software development for data recovery and forensic analysis. He has more than 15 years of experience in this field.
LinkedIn:






