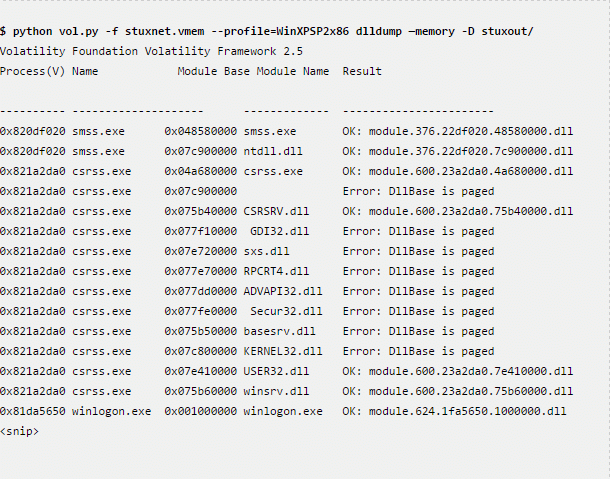
Andrew Case released a fresh blog post at Volatility Labs. He covers how to automate the detection of previously identified malware through the use of three Volatility plugins along with ClamAV. Although this walk-through primarily focuses on Windows memory samples, at the end he explains how to port the approach to Linux and OS X samples.
Use this link to read full post.