Over the past twenty years, the number of cyber extortion incidents has risen sharply. In fact, the FBI identified online extortion as the second highest cybercrime complaint received in 2024. What makes cyber extortion particularly unique is the emotional and psychological harm weaponized against victims for financial gain. That’s why cybercrime awareness is vital. Education is one of our strongest defenses against internet extortion, and this article is the perfect place to start.
What is Cyber Extortion?
Cyber extortion is a crime in which someone performs or threatens an undesired action against an individual or group. The criminals will then make demands and promise to make good on their threat unless the victim complies. Oftentimes, the criminal has access to valuable data that they use as leverage to extort the victim.
Common Tactics Used in Cyber Extortion Threats
There are numerous ways in which the cybercriminal can come into possession of this leverage. Some attackers may hack into databases to steal valuable data. Others may trick the victim into volunteering their data by posing as someone the victim may trust. The strategy used by the perpetrator to obtain data is often determined by who their target is. The more technical tactics are reserved for organizations with sophisticated cybersecurity.
Hacking Tactics
Rather than getting the victim to offer up information, hackers take the information by working around the organization’s security. Attackers bypass security measures through tactics such as malicious software or stolen credentials that enable them to extract records.
This could be done by sending an email to potential victims that contains malware in an attachment or link. They can also gain unauthorized access through brute-force attacks like credential stuffing.
Impersonation or Fraud Tactics
Impersonation scams intend to lure the victim to willingly pass their data along to the cyber extortionist. This is done by giving off the façade of being someone else. This can be done in numerous ways, but the two most popular methods are spoofing and catfishing.
- Spoofing. Criminals may pose as a trusted entity or individual to trick the victim into confiding in the extortionist. Spoofing is a method criminals use to disguise themselves. The perpetrator may spoof a legitimate website to capture information or spoof an email, mimicking a real address.
- Catfishing. This is the process of creating a fake identity that appeals to the victim’s yearnings. Catfish often pose as highly desirable individuals and potential romantic partners.
Social Engineering
Social engineering is the process of using manipulation to gain access to private data required for extortion. Extortionists use this strategy against individuals, as it doesn’t require the technical knowledge of hacking. There are many types of social engineering, but some of the more popular tactics are listed below.
- Phishing. Similar to spoofing, phishing involves sending a message, under the guise of a trusted entity, to an individual. Then, the cyber extortionist will attempt to gain access to login credentials and other private information.
- Vishing and Smishing. Vishing, also known as voice phishing, occurs over phone calls or voice messages. Smishing, also known as SMS phishing, occurs over text messages. These social engineering tactics are based on sending messages that appear to come from a trusted source.
- Baiting. A criminal may leave a storage device in a public location, hoping that someone may pick it up. However, the device is infected with malicious software that gives the perpetrator access to the victim’s data.
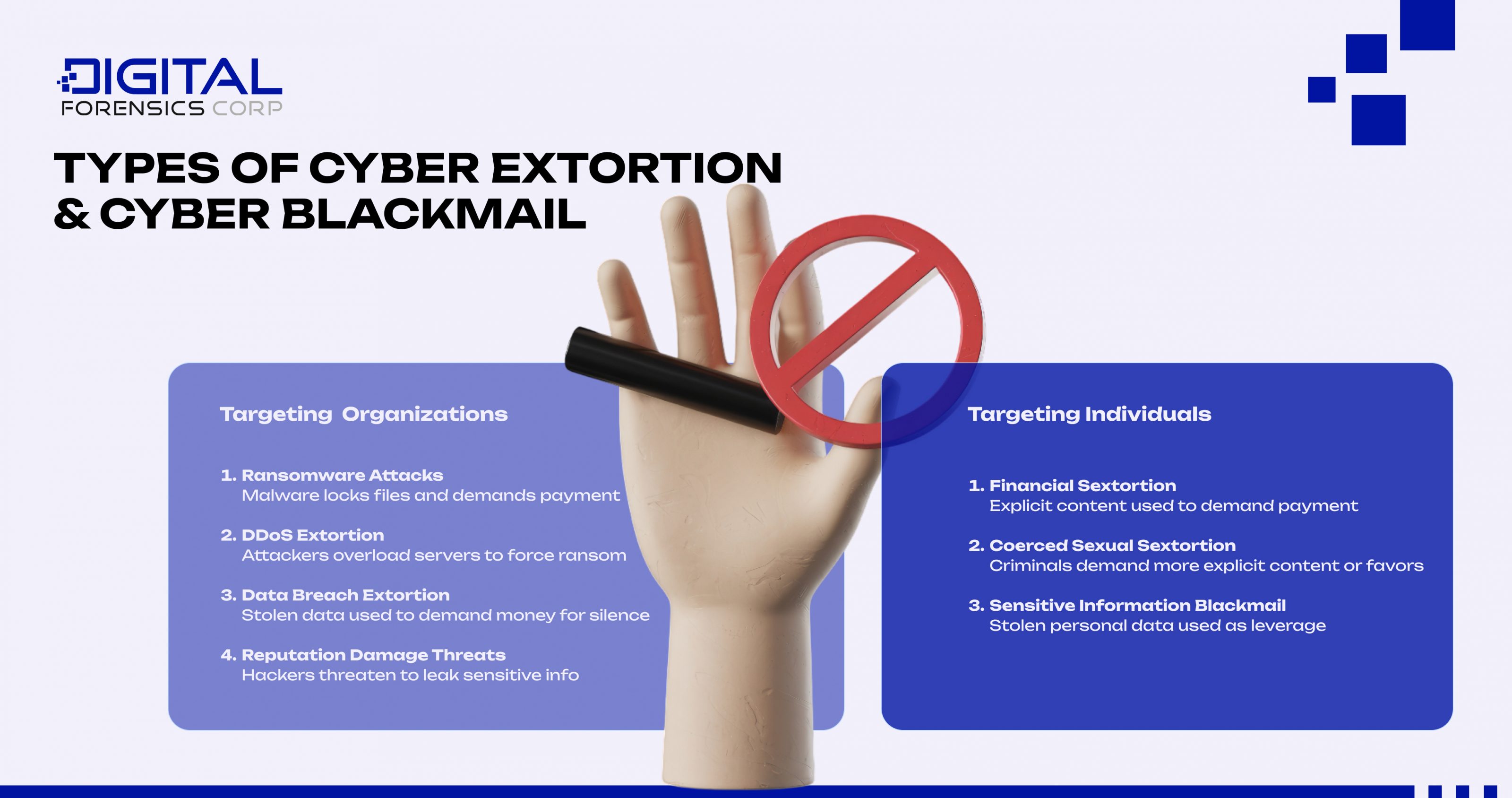
Different Types of Cyber Extortion and Cyber Blackmail
An extortionist will use your data, files, or systems against you. That is why strong security protocols are important. There are cases where perpetrators will fabricate compromising images or videos to extort victims. However, most cybercriminals will attempt to gain access to a victim’s protected data because it’s far more effective. Cyber extortion and cyber blackmail generally target two groups: organizations and individuals.
Organizations
- Ransomware – The perpetrator utilizes malicious software to lock the victim’s files and “hold them for ransom”. They will proceed to hold this data hostage as a means of leverage in their attempt to extort the victim.
- Distributed Denial of Service (DDoS) – Extortionists, either manually or through using bots, overload a website’s server to block potential visitors from access. They will then threaten to continue flooding the server until the victim succumbs to the extortion.
- Data Breach Extortion. For businesses, data breaches can be devastating. They can harm a company’s reputation and lead to financial losses. However, in some cases, hackers will steal information and then demand money from the business to keep it private.
- Reputation damage: Exposure of sensitive information can erode trust and credibility
Individuals
- Sextortion (Financial Sextortion) – This form of extortion specifically involves using a victim’s content, explicit photos or videos as leverage. Then, the criminal coerces the victim into paying them to keep their intimate content private.
- Coerced Sexual Sextortion (Sexual Extortion) – This crime also involves the use of a victim’s explicit content as leverage for extortion. However, instead of demanding crypto or gift cards, these criminals demand more sexual content or favors.
- Sensitive Information Blackmail (Hacked and Blackmeiled) – The cybercriminal hacks your account or gains access to your private data using one of the tactics previously discussed. They then use this private data to virtually extort the victim with the threat of misusing the stolen information.
Understanding Cyber Extortion Through Real-World Examples
Sharing our difficult experiences allows us to assist others in avoiding the same mistakes. While understanding online extortion in theory is important, real-life cases can offer more insight into the crime. There are nuances that can be captured in the stories of victims, which can serve as cautionary tales. They can also aid us in better understanding what users should expect from cybercriminals.
Coinbase Data Breach
In May 2025, a cybercrime group managed to bribe Coinbase’s overseas support agents to collect and share sensitive information. The bribed agents stole the data of over 69,000 customers. While they couldn’t collect passwords or funds, they did access the customers’ contact and bank account information.
The cybercrime group used the data to impersonate Coinbase employees and attempted to trick victims into transferring crypto funds. The hacking group also demanded $20 million from Coinbase to keep the attack private. Coinbase refused to comply and instead announced a $20 million reward for any information regarding the group behind the attack.
An Attack Against Travelex
Travelex, a foreign exchange company, was hit with a cyber attack going into the year 2020. The company was infected with ransomware which affected some of Travelex’s services. They were forced to take their services offline as a precaution, leading to customer outrage on social media.
The hackers responsible demanded millions of dollars for the decryption key and to keep the stolen customer data private. Some sources have claimed that the company paid the hackers $2.3 million to restore their data. It wasn’t until January 17th that the company would be able to get customer-facing services going again.
Police Officer Investigated for Sexploitation
In July 2020, a teacher received a message from what she believed to be Snapchat to save her account. She entered her password without thinking but soon after, received a message saying, “I have videos of you.”
The perpetrator then sent a sexually explicit video of the victim that had only been saved on Snapchat. He threatened to send the video to the teacher’s co-workers, loved ones, and friends. He claimed he would keep the video private as long as the teacher sent him more explicit content. She didn’t give in and in response, the perpetrator sent the video to a loved one and posted it online.
Police later identified the culprit as a Louisville Metro police officer named Bryan Wilson. Wilson had used police resources to access information about potential victims. Then, he worked with a hacker to target the women’s private Snapchat accounts, looking for explicit content.
He would then use the content for sexploitation. The officer threatened to send the videos to loved ones unless the women sent him more sexual material. He targeted over twenty women in total. In 2022, Wilson was sentenced to 30 months in prison for civil rights violations regarding a separate incident and cyberstalking conspiracies.
Victim Support: Where to Find Cyber Extortion Help
It can be difficult for victims to know how to handle online extortion threats. Despite the best preventive measures, cyber-attacks can still occur. However, there are organizations and companies that can aid or guide you on how to handle the situation.
- Cyber Civil Rights Initiative (CCRI). This organization combats online abuses that threaten civil rights and liberties. The CCRI has educational resources about nonconsensual distribution of intimate images and the legal landscape concerning the crime. The organization has an image-abuse helpline to support victims at (844) 878-CCRI.
- The Cyber Helpline. This nonprofit supports victims of cybercrime with expert assistance at any time. There is a chatbot, 24/7 helpline, and educational resources for additional assistance. The Cyber Helpline is available in the UK and USA.
- Resources for Minors (NCMEC). The National Center for Missing and Exploited Children (NCMEC) is a nonprofit made to protect minors. The NCMEC has a Cybertipline, which is the centralized reporting system for cases of minors affected by CSAM. All complaints to the Cybertipline are shared with the appropriate law enforcement agency. The NCMEC also has a 24/7 helpline for victim support at 1-800-THE-LOST.
What to Do When Facing Cyber Extortion
If you are a victim of digital extortion, there are measures you can take to regain control. Internet extortion is a serious threat and needs to be handled accordingly. While the situation is scary, you need to try to remain level-headed and take a rational approach. Acting swiftly and proceeding with the following course of action is advised:
- Don’t Pay the Extortionist. Meeting their demands will not stop the extortion. It will only lead to further threats and demands. Cybercriminals should not be trusted at their word – in fact, most don’t follow through on their threats. Instead, use stall tactics to buy yourself time and reach out to law enforcement or cybersecurity experts for support.
- Collect Evidence Immediately. You need to gather proof of the crime. This includes accounts, communication logs, and any other data that can assist you in taking legal action.
- Secure Your Online Presence. Update your passwords and privacy settings for any online accounts that the scammer could have access to. You should also verify that no unauthorized users have access. Make sure to enable two-factor authentication to prevent further security incidents.
- Reach Out to Private Cybersecurity Firms. Certain firms specialize in assisting victims of digital extortion. They prioritize protecting the privacy of victims and mitigate any exposure that could possibly happen. Digital forensic experts can also trace the perpetrator’s online footprint, collecting evidence for victims to use for legal action.
How to Report Cyber Extortion and Cyber Blackmail
Many victims remain silent because they feel embarrassed or they don’t recognize the importance of reporting crimes. Not only does notifying the authorities of online extortion benefit victims, but it also assists law enforcement in tracking patterns. Filing a complaint with the police allows you to create a legal record of the crime, preserving your evidence. The complaint may also launch an investigation, or it may fit into an ongoing operation.
Notifying the FBI
While local law enforcement agencies are invaluable to victims of extortion, they also have limited jurisdiction. This is why you should also notify the FBI of online extortion. The FBI runs the Internet Crime Complaint Center (IC3), the national hub for reporting cybercrime. The IC3 is not limited to local jurisdiction and can even work with international police to target cybercriminals in other countries. However, it’s important to note that law enforcement often handles high caseloads. This can lead to delays, even as victims continue to face constant threats.
Consider the Benefits of Working with Digital Forensics Professionals
If you are a victim of digital extortion, reach out to Digital Forensic Corp. for expert support. We are a private cybersecurity firm that specializes in assisting extortion victims. Our team is well-versed in cybercriminal tactics and understands how to put an end to the ongoing threats. Don’t let cybercriminals catch you off guard. Contact our Blackmail Helpline for a free consultation.






